38 security labels are used in what type of model
6 Steps in Asset Tagging Process Flow - Camcode Asset tagging is the process of affixing identification tags or labels, also known as asset tags, to assets. Asset tagging is used for both fixed and moveable assets to provide a way to identify individual assets throughout their useful life. Amazon.com: Uniclife 28-Key Steel Key Cabinet with Combination … Secure Construction: 8" L x 3" W x 9.8" H. Made of 0.8 mm heavy-duty frosted steel sheet for optimal security. And the solid piano hinge makes it unlikely to be pried open to avoid forced entry. 28 Tags in 5 Colors: Contain 28 larger but light key tags with labels to write and clear windows for easy visibility. Easily identify keys by both ...
Simple Ways to Install Security Cameras (with Pictures) - wikiHow 07.07.2022 · Usually, the quality of a security camera is reflected in its price. If it’s a relatively inexpensive model, this most likely means that it’s not as high-quality or as effective as other security cameras. That being said, don’t simply buy the most expensive camera you can find. Base your judgment on what features the camera has and on how ...

Security labels are used in what type of model
Evaluate Model: Component Reference - Azure Machine Learning 10.11.2021 · Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models Microsoft creates new self-service sensitivity labels in Microsoft 365 At Microsoft, there are four labels used for container and file classification: Highly confidential. The most critical data for Microsoft. Share it only with named recipients. Confidential. Crucial to achieving Microsoft's goals. Limited distribution—on a need-to-know basis. General. Classification: True vs. False and Positive vs. Negative A true positive is an outcome where the model correctly predicts the positive class. Similarly, a true negative is an outcome where the model correctly predicts the negative class.. A false positive is an outcome where the model incorrectly predicts the positive class. And a false negative is an outcome where the model incorrectly predicts the negative class.. In the following sections, we'll ...
Security labels are used in what type of model. What is the basis on which Brocade switch models are determined? Determining the Brocade switch type based on the output of the switchshow command: Use the following chart to determine the model number of the SilkWorm switch, based on the switch type: Sikworm Model Number (Switch Type ) Switch Type. 1000. 1. What Is Data Labelling and How to Do It Efficiently [2022] - V7Labs Data labeling refers to the process of adding tags or labels to raw data such as images, videos, text, and audio. These tags form a representation of what class of objects the data belongs to and helps a machine learning model learn to identify that particular class of objects when encountered in data without a tag. Power BI security white paper - Power BI | Microsoft Learn The decades-old foundations of the BI security model - object-level and row-level security - while still important, clearly no longer suffice for providing the kind of security needed in the cloud era. Instead, organizations must look for a cloud-native, multi-tiered, defense-in-depth security solution for their business intelligence data. Accessibility | Vue.js You can see the description by inspecting Chrome DevTools: Placeholder #. Avoid using placeholders as they can confuse many users. One of the issues with placeholders is that they don't meet the color contrast criteria by default; fixing the color contrast makes the placeholder look like pre-populated data in the input fields. Looking at the following example, you can see …
Creating and managing labels | Resource Manager … Vor 2 Tagen · Team or cost center labels: Add labels based on team or cost center to distinguish resources owned by different teams (for example, team:research and team:analytics). You can use this type of label for cost accounting or budgeting. Component labels: For example, component:redis, component:frontend, component:ingest, and component:dashboard. 5 Access Control Types: RBAC, ABAC, MAC, RuBAC, and DAC Compared In computer security, an access-control list (ACL) is a list of rules and permissions for managing authorization. This means ACL specifies which users are allowed to access specific system resources or platforms. In addition, ACL helps administrators monitor user access in many businesses. Publish and apply retention labels - Microsoft Purview (compliance ... You can apply retention labels to Outlook folders as a default label that can be inherited by messages in that folder. Right-click the folder, select Properties, the Policy tab, and select the retention label you want to use as that folder's default retention label. Use a custom TensorFlow Lite model with Flutter - Firebase Use a custom TensorFlow Lite model with Flutter bookmark_border On this page TensorFlow Lite models Before you begin 1. Deploy your model 2. Download the model to the device and initialize a...
Locating the Vehicle Emissions Label | US EPA Locating the Vehicle Emissions Label. EPA's vehicle emissions label is titled: "Vehicle Emission Control Information" and it contains. an unconditional statement of compliance with EPA emission regulations. The images below show an example of the label used for model year vehicles produced before and after 2007. 4 Types of Inventory Control Systems - Camcode Barcode labels serve as inventory trackers, allowing users to bring up information about the item on a computer system, such as the item's price, the number of items in stock, the location of an item within a warehouse, and more. IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers This work role conducts comprehensive assessments of the management, operational, and technical security controls to determine their overall effectiveness. 6. Put the steps in the Threat Modeling process into the correct order. (Not all options are used.) IoT Security (Version 1.0) - IoT Fundamentals: IoT Security Final Exam 38 7. Classification in Machine Learning: What it is and Classification Models In classification, a program uses the dataset or observations provided to learn how to categorize new observations into various classes or groups. For instance, 0 or 1, red or blue, yes or no, spam or not spam, etc. Targets, labels, or categories can all be used to describe classes. The Classification algorithm uses labeled input data because ...
What is MPLS, and why isn't it dead yet? | Network World The MPLS Label consists of four sub-parts: The Label The label holds all of the information for MPLS routers to determine where the packet should be forwarded. Experimental Experimental bits are...
Introduction To Classic Security Models - GeeksforGeeks These models are used for maintaining goals of security, i.e. Confidentiality, Integrity, and Availability. In simple words, it deals with CIA Triad maintenance. There are 3 main types of Classic Security Models. Bell-LaPadula Biba Clarke Wilson Security Model 1. Bell-LaPadula
Security Market Line (SML) Definition and Characteristics - Investopedia The security market line (SML) is a line drawn on a chart that serves as a graphical representation of the capital asset pricing model (CAPM) —which shows different levels of systematic, or market...
Evaluate Model: Component Reference - Azure Machine Learning Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models
Using RFID for Inventory Management: Pros and Cons - Camcode Most tags used for inventory tracking are passive RFID tags, meaning they contain no battery and are powered by the waves from the readers. Active tags are powered, come at a higher cost, and are used for long-range tracking of machineries such as trucks and railway cars. Pros in Using RFID Tags for Inventory Management
7 Layers of The OSI Model (A Complete Guide) - Software Testing Help Here are the 7 Layers of the OSI Model: #1) Layer 1 - Physical layer. The physical layer is the first and bottom-most layer of the OSI Reference Model. It mainly provides the bitstream transmission. It also characterizes the media type, connector type and signal type to be used for communication.
Avery Printable Shipping Labels with Sure Feed, 3-1/3" x 4", White, … Make sure this fits by entering your model number. Reuse packaging again and again with our True Block technology that completely covers old shipping labels, markings and everything underneath the label ; Get a more reliable feed through your laser printer with printable label sheets featuring proprietary Sure Feed technology ; Customize mailing address labels by …
Why do we have four levels of security in Power BI? Do not use None to avoid unwanted side effects, like the passing of data between data sources. Row-Level-Security (RLS) in Power BI models. Row-Level-Security (RLS) controls who has access to which data in the data model. This feature of Power BI is well documented and understood in the community. There are three forms of this feature:
How open-source data labeling technology can mitigate bias It's an approach that Malyuk said can potentially identify bias for a specific label. The open-source Label Studio technology is intended to be used by individuals and small groups, while the...
7 Types of Organizational Structures for Companies - Creately Blog The hierarchical model is the most popular organizational chart type. There are a few models that are derived from this model. In a hierarchical organization structure, employees are grouped with every employee having one clear supervisor. The grouping is done based on a few factors, hence many models are derived from this.
How to apply sensitivity labels in Power BI - Power BI Sensitivity labels from Microsoft Purview Information Protection on your reports, dashboards, datasets, dataflows, and .pbix files can guard your sensitive content against unauthorized data access and leakage. Labeling your data correctly with sensitivity labels ensures that only authorized people can access your data.
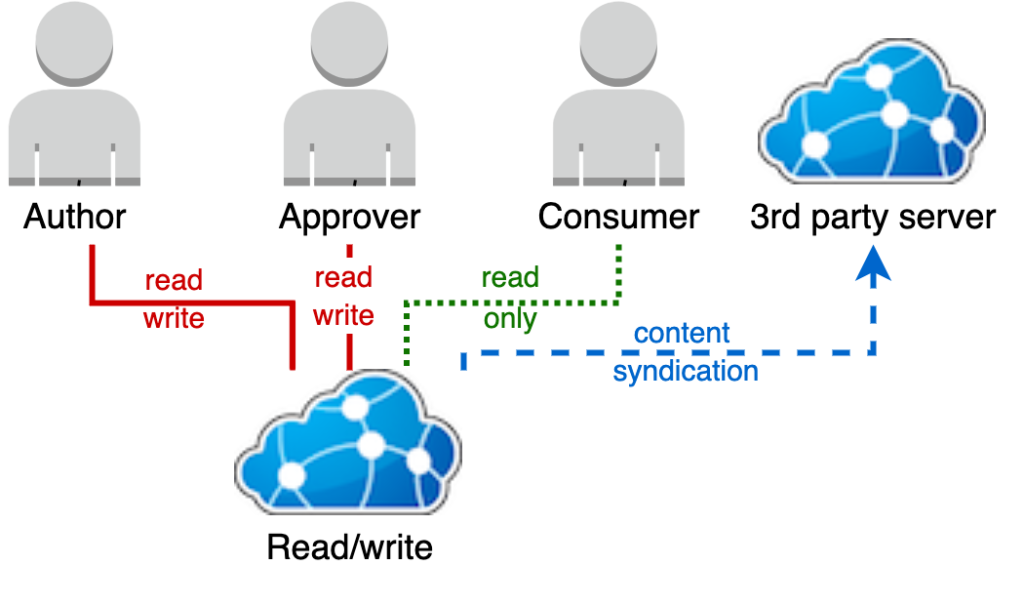
Which type of access control model assigns security level labels to ... attribute-based Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications.
REST API Security Essentials 2. Best Practices to Secure REST APIs. Below given points may serve as a checklist for designing the security mechanism for REST APIs. 2.1. Keep it Simple. Secure an API/System - just how secure it needs to be. Every time you make the solution more complex "unnecessarily," you are also likely to leave a hole. 2.2.

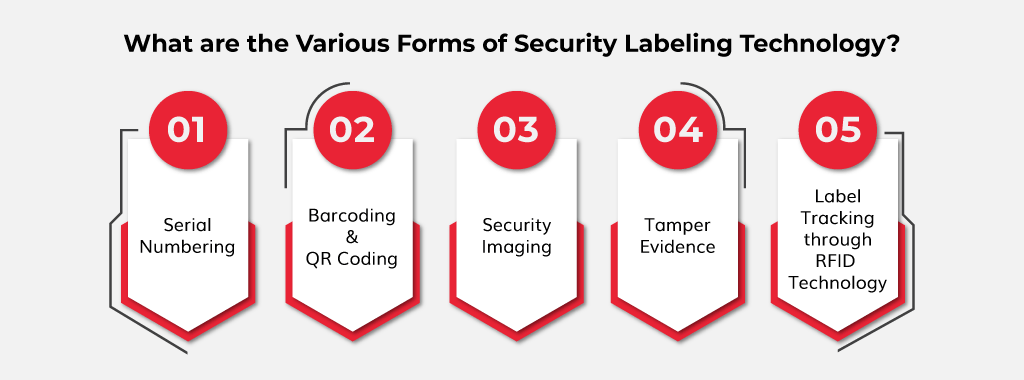
100 Total Transfer Tamper Evident Security Warranty Void Stickers/ Labels/ Seals (Red, 30x90 mm, Serial Numbers - TamperSTOP)
The Best Label Makers for 2022 | PCMag The LabelWorks LW-PX400 is equally ready to work at your home, work desk, or work site. For desktop use, it comes with an AC adapter, doesn't take up much room (it's 5.6 by 2 by 5.6 inches, HWD),...
Moderate, classify, and process documents using Amazon Rekognition and ... The notebook demonstrates the entire lifecycle of preparing training and test images, labeling them, creating manifest files, training a model, and running the trained model with Rekognition Custom Labels. Alternatively, you can train and run the model using the Rekognition Custom Labels console. For instructions, refer to Training a model ...
ITIL security management - Wikipedia ITIL security management describes the structured fitting of security into an organization.ITIL security management is based on the ISO 27001 standard. "ISO/IEC 27001:2005 covers all types of organizations (e.g. commercial enterprises, government agencies, not-for profit organizations). ISO/IEC 27001:2005 specifies the requirements for establishing, implementing, …
How to label your data for Custom Named Entity Recognition (NER ... Model performance is dependent on possible ambiguity in your schema, and the quality of your labeled data. Nevertheless, we recommend having around 50 labeled instances per entity type. Label your data Use the following steps to label your data: Go to your project page in Language Studio. From the left side menu, select Data labeling.

100pcs Non Transfer Tamper Evident Security Warranty "VoidOpen" Labels/ Stickers/ Seals for Reusable Package and Expensive Surface (Red, 1 x 3.35 ...
Classification: True vs. False and Positive vs. Negative A true positive is an outcome where the model correctly predicts the positive class. Similarly, a true negative is an outcome where the model correctly predicts the negative class.. A false positive is an outcome where the model incorrectly predicts the positive class. And a false negative is an outcome where the model incorrectly predicts the negative class.. In the following sections, we'll ...
Microsoft creates new self-service sensitivity labels in Microsoft 365 At Microsoft, there are four labels used for container and file classification: Highly confidential. The most critical data for Microsoft. Share it only with named recipients. Confidential. Crucial to achieving Microsoft's goals. Limited distribution—on a need-to-know basis. General.
Evaluate Model: Component Reference - Azure Machine Learning 10.11.2021 · Use this component to measure the accuracy of a trained model. You provide a dataset containing scores generated from a model, and the Evaluate Model component computes a set of industry-standard evaluation metrics. The metrics returned by Evaluate Model depend on the type of model that you are evaluating: Classification Models; Regression Models

860-960MHz anti theft label stickers UHF RFID security tags for jewelry paper adhesive for jewel shop store management

100pcs Non Transfer Tamper Proof Security Warranty "VoidOpen" Labels/ Stickers/ Seals for Reusable Package or Expensive Surface (Blue, 1 x 3.35 ...



























Post a Comment for "38 security labels are used in what type of model"