38 security labels access control
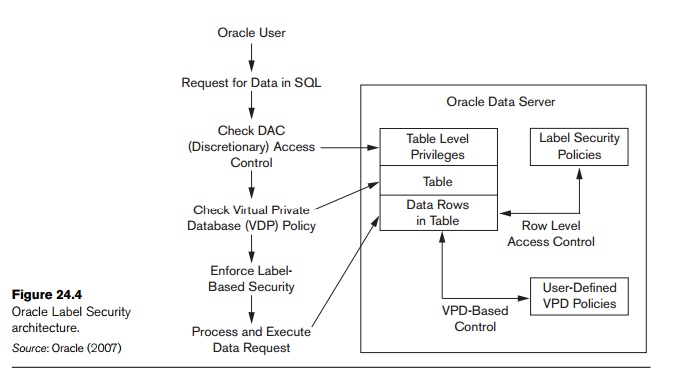
Learn about sensitivity labels - Microsoft Purview (compliance) This label configuration doesn't result in documents or emails being automatically labeled but instead, the label settings protect content by controlling access to the container where content can be stored. These settings include privacy settings, external user access and external sharing, and access from unmanaged devices. Label Security | Oracle Oracle Label Security Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
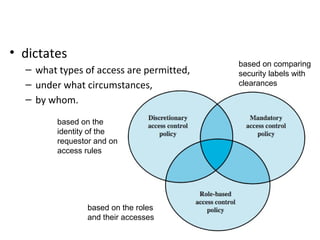
Which of the following access control models use security labels to ... Mandatory access control (MAC) Role-based access control (RBAC) Identity-based access control (IBAC) Discretionary access control (DAC) Explanation: MAC uses security labels for access decisions. More Questions: CCNA SECFND 210-250 Dumps - Certification Practice Exam Answers. 0 Comments.
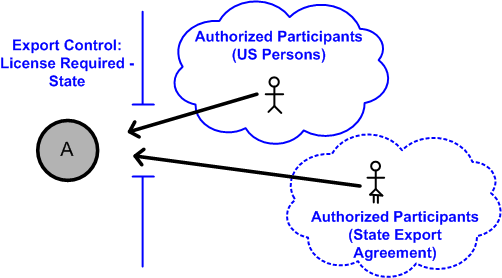
Security labels access control
Label Control (Access) | Microsoft Learn A label can be attached to another control. When you create a text box, for example, it has an attached label that displays a caption for that text box. This label appears as a column heading in the Datasheet view of a form. When you create a label by using the Label tool, the label stands on its own — it isn't attached to any other control. Mandatory Access Control - Trusted Extensions User's Guide - Oracle Mandatory access control (MAC) is a system-enforced access control mechanism that is based on label relationships. The system associates a sensitivity label with all processes that are created to execute programs. MAC policy uses this label in access control decisions. Security Labels - PolyLabel.com Please feel free to contact PolyLabel.com to discuss the various options you have to security your assets with our labels. We can be reached directly at 1-519-743-3422 or use our Label Request form. Post Views: 1,271 Author Poly Label
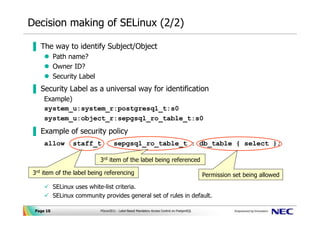
Security labels access control. Access Control for Property Graph Data (Graph-Level and OLS) However, for applications with stringent security requirements, you can enforce a fine-grained access control mechanism by using the Oracle Label Security option of Oracle Database. With OLS, for each query, access to specific elements (vertices or edges) is granted by comparing their labels with the user's labels. (For information about using ... Contact security - Oracle Contact security, also known as Label-Based Access Control (LBAC), allows you to use labels to manage access to contacts in your database. Note: Contact security is part of the Oracle Eloqua Security Administration Cloud Service and is included in the Standard and Enterprise trims. Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label. Mandatory Access Control: How It Works - Firewall Times Mandatory access control relies on a system of security labels. Every resource under MAC has a security classification, such as Classified, Secret, and Top Secret. Likewise, every user has one or more security clearances. To access a given resource, the user must have a clearance matching or exceeding the resource's classification.
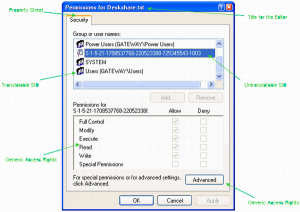
LBAC - Label Based Access Control - DataGeek.blog Label Based Access Control essentially adds a column to a table that labels each row (think confidential, secret, top secret), and then grants uses of those labels to users to allow them to access the data. Complex hierarchical structures are possible, and some planning is needed to work things out. Specialist for the identification of luggage and products | Security Label RFID Labels - Take a big step forward with Security Label now. RFID Labels make your business more efficient. Whether product and baggage identification, access control, stock-taking or logistics processes - Security Label offer you numerous solutions that can be customized for your company. Find out more about our RFID Labels. How security labels control access - ibm.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
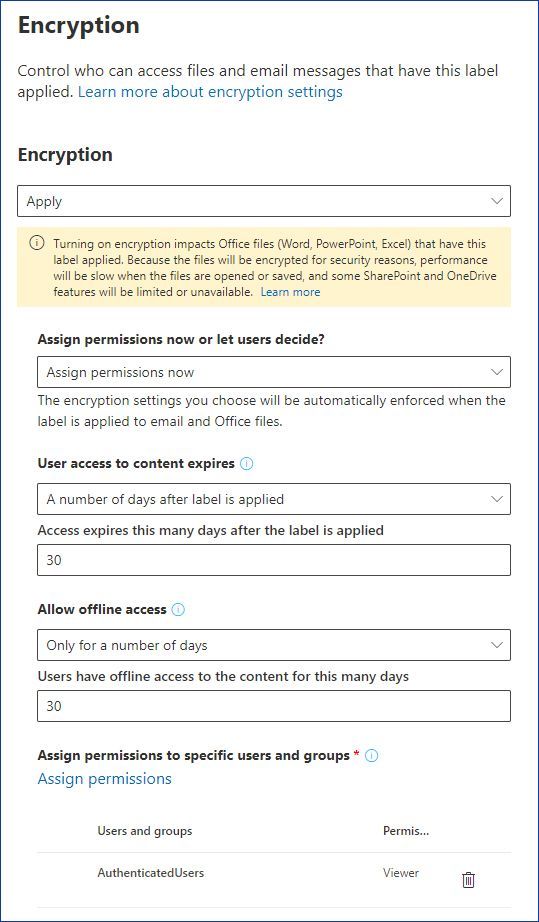
Access Control Models - CompTIA Security+ SY0-501 - 4.3 It's either confidential, or secret, or top secret, or some other type of label. The users then are provided with certain rights. Certain users can access confidential objects. ... But it's also a very weak form of access control security because it relies on the owner of the file to be setting the proper security for that particular object ... Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. Oracle Label Security Oracle Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database. Secure external collaboration using sensitivity labels In addition to that, it is possible to make the protected content time-bound as well as control whether users can access it offline and for how long. In this case your label may look like this: Figure 3: A sensitivity label granting Authenticated users view-only access.
Security Labels - PolyLabel.com Please feel free to contact PolyLabel.com to discuss the various options you have to security your assets with our labels. We can be reached directly at 1-519-743-3422 or use our Label Request form. Post Views: 1,271 Author Poly Label
Mandatory Access Control - Trusted Extensions User's Guide - Oracle Mandatory access control (MAC) is a system-enforced access control mechanism that is based on label relationships. The system associates a sensitivity label with all processes that are created to execute programs. MAC policy uses this label in access control decisions.
Label Control (Access) | Microsoft Learn A label can be attached to another control. When you create a text box, for example, it has an attached label that displays a caption for that text box. This label appears as a column heading in the Datasheet view of a form. When you create a label by using the Label tool, the label stands on its own — it isn't attached to any other control.


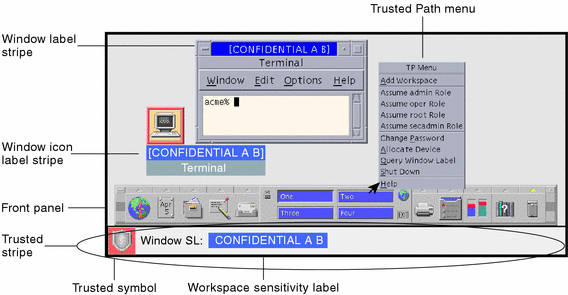
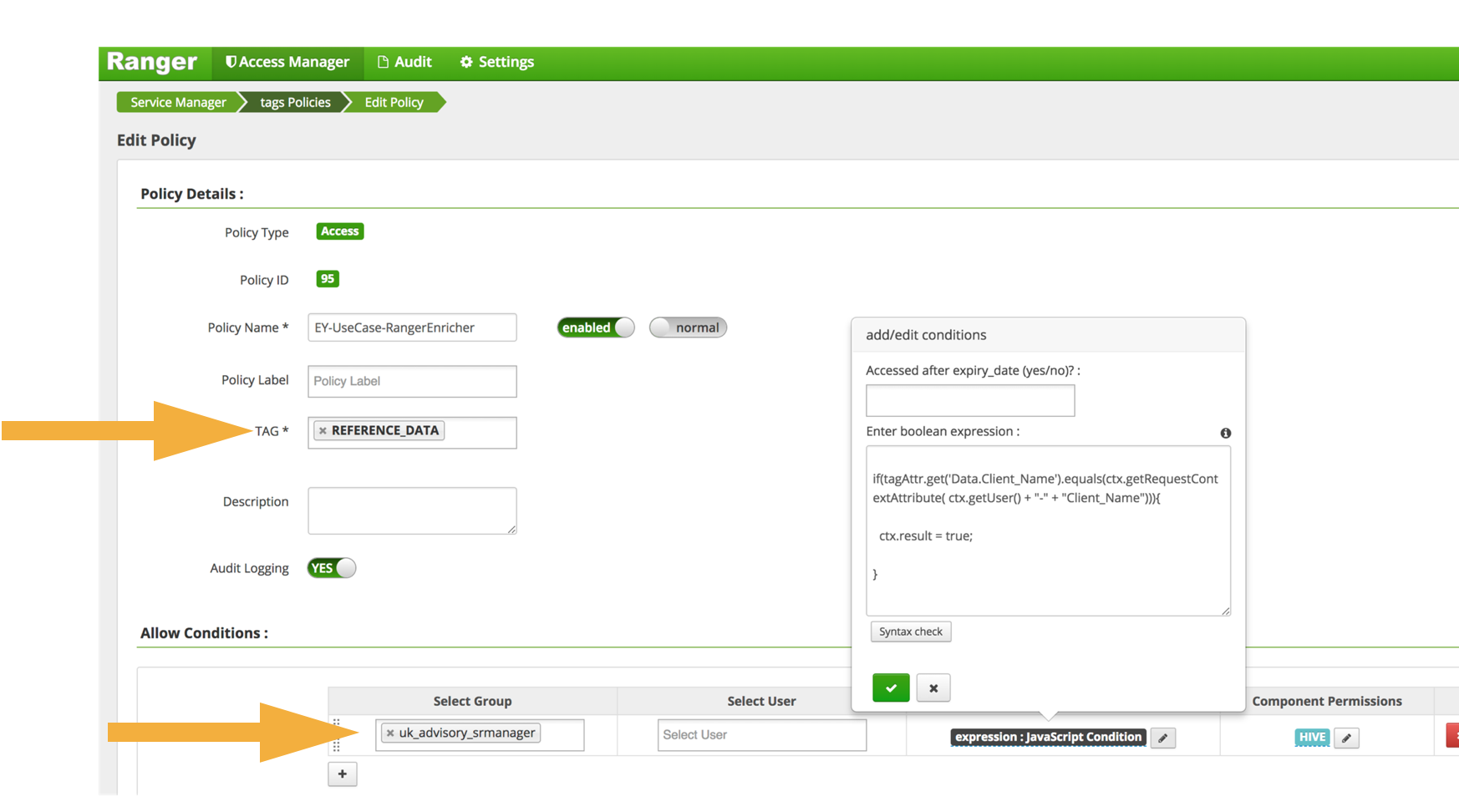








!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)










Post a Comment for "38 security labels access control"